A secure design of crypto custody with TEE
A friend of mine, an early Bitcoin adopter, always believed in self-sovereignty. “Not your keys, not your coins,” he would say. But as the years passed, the risks grew. Hacks, phishing attacks, even forced seizures, he had seen it all.
He prided himself on keeping his assets secure. He had hardware wallets, multisig setups, and backups. But deep down, he knew there was still a flaw: trust.
Trust in third-party firmware. Trust in cloud-based recovery solutions. Trust in the fact that his keys, even if protected, were still a single point of failure.
One night, he called me.
“I want a setup that no one, not hackers, not corporations, not even a government, can break. And I want to keep it in my own hands.”
“Can you do something for it?” he asked me.
I think the better way is warm wallets with TEE at home. Instead of relying on a single hardware wallet or a custodial service, I showed him how his private keys could be split into multiple secure enclaves, running across devices he controlled—his home server, a Raspberry Pi, even a friend’s node.
TEE (Trusted Execution Environment) ensures that no one device ever sees the full key. GNU Artanis secures the communication between them, preventing tampering and leaks. Even if one part was stolen, hacked, or seized, it would be useless on its own.
“This means… even if my laptop was stolen, they still can’t take my funds?” he asked.
“Exactly. And you don’t have to trust me, or anyone, to do it.”
Hot wallet, warm wallet, and cold wallet
A hot wallet is a wallet that is connected to the internet. It is used for day-to-day transactions and is convenient but risky.
A warm wallet is a wallet that is not connected to the internet but is still accessible. It is used for storing funds that you might need to access quickly.
A cold wallet is a wallet that is completely offline. It is used for storing large amounts of funds that you do not need to access often.
If we want to avoid to rely on any third-party service, we need to build a warm wallet with TEE at home. The basic idea is to send your funds from you own device to public exchange service when you need to trade. The funds are stored in your own device and you can access them anytime. This prevent you to reply on any third-party service and send all your funds to them.
TEE is a technology that can protect your private keys from being stolen. It is a secure environment that is isolated from the rest of the system. It can be used to store your private keys and sign transactions without exposing them to the outside world.
Furthermore, TEE can be used to encrypt your system, even if your device is stolen, the attacker can't access your data include private keys.
That's why A16Z invested in TEE. They believe that TEE will be a key technology for securing the future of crypto custody.
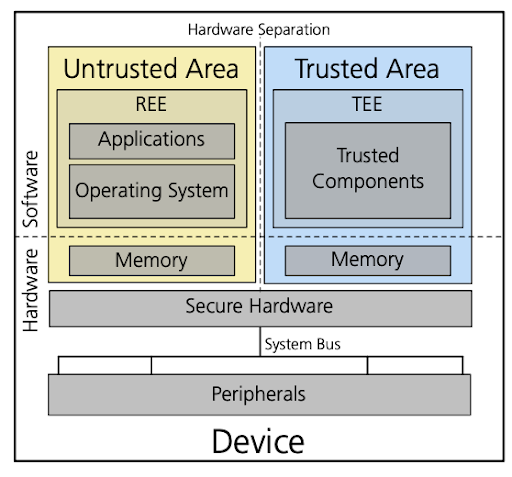
Figure 1: TEE architecture
GNU Artanis custody solution
GNU Artanis is a web application framework written in Guile Scheme. It's both GNU and HardenedLinux official project. It's designed to be secure and easy to use.
In our GNU Artanis custody solution, we use GNU Artanis to build a secure service between RESTful, database, TEE and public exchange service.
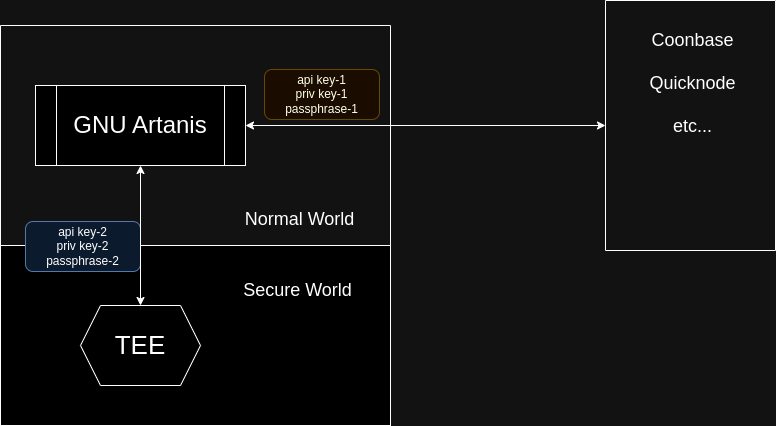
Figure 2: Artanis custody architecture
To implement the custody solution, we need at least two triplets of credentials. The first triplet is the public exchange service credentials, the second triplet is the local credentials stored in TEE.
So what's the triplet?
- API key
- Private key
- Passphrase
In modern authentication, the API key is used to authenticate the user to the service. The private key is used to sign the transaction. The passphrase is used to encrypt the private key.
The security best practices
As mentioned, GNU Artanis is HardenedLinux official project. HardenedLinux is a security-focused collection of best practice. It provides a secure environment for running GNU Artanis.
HardenedLinux is in a heavy development phase to adapt to TEE in a new hardware platform. We're working on it and will provide more details in the future.
Besides, HardenedLinux provides Linux Kernel Vaccine, which is a security module that can protect the system from being attacked. This is named as VED (Vault Exploit Defense). In the past system integration test, VED has been around only 3%~5% overhead for GNU Artanis application. However, it provides a very high rate of protection for 0day exploit.
About VED
So far, there are only three runtime protection product in the world, which are GRSecurity, Hitachi AKO, and VED,
GRSecurity is the top one, and it's GPL licensed. The most expensive solution, of course.
AKO stands for Additional Kernel Observer, which was developed by Hitachi. It's proprietary software. And mainly designed and used for Hitachi's own product.
VED is the third one, which is GPL licensed. It's developed by HardenedVault, and HardenedLinux has a community edition. It's the most cost-effective solution.
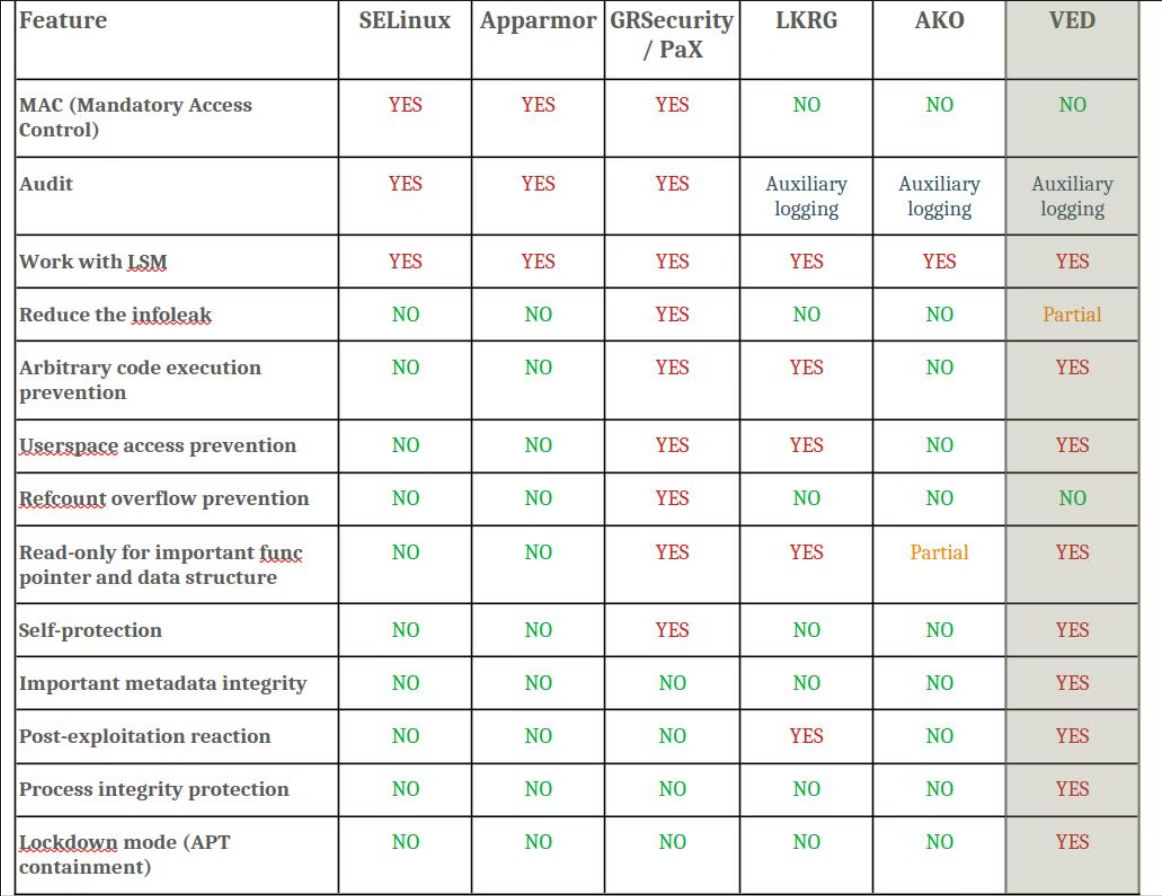
Figure 3: Runtime protection solution comparison
The transaction flow
- The user sends a request to the GNU Artanis service.
- The GNU Artanis service sends a request to the TEE.
- The TEE signs the transaction with the private key.
- The TEE sends the signed transaction back to the GNU Artanis service.
- The GNU Artanis service sends the signed transaction to the public exchange service.
- The public exchange service verifies the signed transaction and processes it.
- The public exchange service sends the result back to the GNU Artanis service.
- The GNU Artanis service sends the result back to the user.
Users will be asked to input the passphrase to decrypt the private key in TEE. The passphrase is never stored in the TEE, it's only used to decrypt the private key.
So we can come to these conclusions:
Conclusion
- The transaction is secure because users will be asked to input the passphrase to decrypt the private key in TEE.
- The user's data (transaction history and trading strategy) and private keys are safe, even if the device is stolen, or the hard disk is taken out.
The roadmap
- Artanis custody plugin (full support coinbsae, quicknode, etc)
- TEE support in HardenedLinux
- Credential management in TEE
- VED integration in HardenedLinux
- Hardware warm wallet solution
Feedback
Welcome to raise issue or PR in Artanis custody plugin.